How to install Traefik on linux / vps
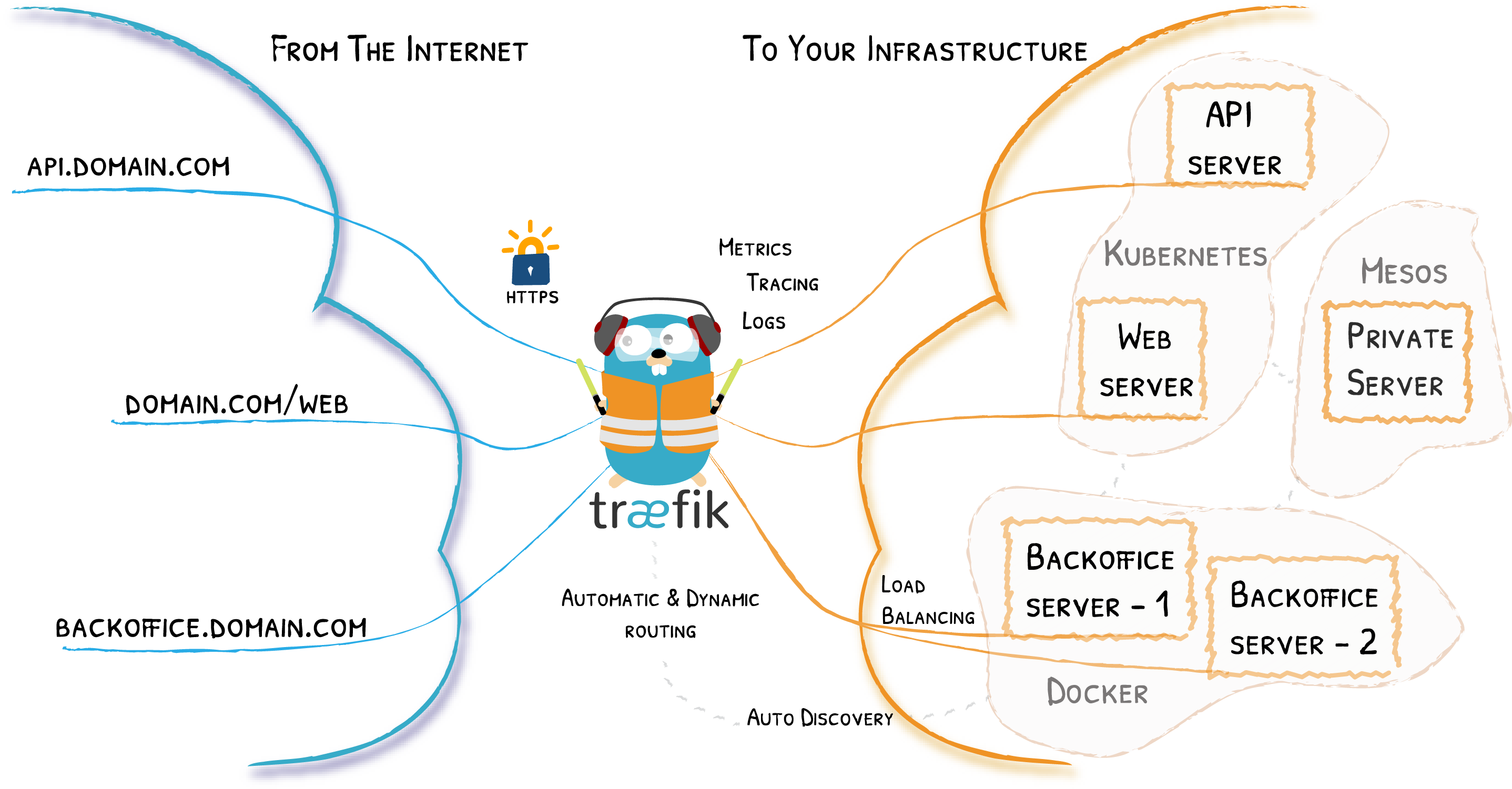
Traefik is a modern HTTP reverse proxy and load balancer that makes deploying microservices easy. With Traefik you can use domain to access your services like for example using https://blog.example.com instead of plain http://192.168.1.1:8080
Traefik is a leading modern open source reverse proxy and ingress controller that makes deploying services and APIs easy. Traefik integrates with your existing infrastructure components and configures itself automatically and dynamically.[1]
Prerequisites

Version used in this documentation
There can be slight differences on installation processes if you are on different versions or hardware
| Application | Version |
|---|---|
| Debian | 11 |
| Linux Docker | 20.10.21 |
| Synology Docker | 20.10.23-1437 |
| Docker Compose | 1.29.2 |
| Portainer | 2.19.5 |
| Traefik | 3.1.1 |
Environments in the examples
Check these if you are not sure which environments you can safely change
| Name | Mapped | Container |
|---|---|---|
| Container name | traefik | |
| Container image | traefik | |
| traefik.yml mount | /volume1/docker/traefik/traefik.yml | /traefik.yml |
| Config directory mount | /volume1/docker/traefik/config | /config |
| Let's encrypt directory mount | /volume1/docker/traefik/letsencrypt | /letsencrypt |
| Http port | 80 | 80 |
| Https port | 443 | 443 |
| Web GUI port | 8080 | 8080 |
How to install Traefik
Prepare the directory and config files
- Prepare the directories for traefik, its config, and letsencrypt certificates
sudo mkdir -p /volume1/docker/traefik/{config,letsencrypt} - In the
/volume1/docker/traefikfolder create atraefik.ymlfilesudo touch /volume1/docker/traefik/traefik.yml` - In the
/volume1/docker/traefik/configfolder create aconfig.ymlfilesudo touch /volume1/docker/traefik/config/config.yml - Fill in the
traefik.ymlwith these:Change every
${}to your valuesglobal: checkNewVersion: true sendAnonymousUsage: false entryPoints: web: address: ":80" websecure: address: ":443" api: insecure: false dashboard: true providers: file: directory: /config watch: true docker: endpoint: "unix:///var/run/docker.sock" exposedByDefault: false certificatesResolvers: myresolver: acme: email: ${YOUR_OWN_EMAIL} storage: /letsencrypt/acme.json - We are not going to fill the
config.ymlfile because in this tutorial we are going to fully utilize docker labels instead of manually configuring the routes. But if you are interested you can read the documentation here
Deploy using Portainer
-
Open portainer i.e.
https://192.168.1.1:10000, click on the environment i.e.local, then click onStacks -
Click
+ Add stackthen fill in the name of yourTraefikstack i.e.Traefik -
Fill the editor with these:
Change every
${}to your valuesversion: '3' services: traefik: container_name: traefik image: traefik restart: on-failure:5 ports: - "80:80" - "443:443" - "8080:8080" volumes: - /var/run/docker.sock:/var/run/docker.sock:ro - /volume1/docker/traefik/config:/config - /volume1/docker/traefik/traefik.yml:/traefik.yml - /volume1/docker/traefik/letsencrypt:/letsencrypt labels: - traefik.enable=true - traefik.http.routers.traefik.rule=Host(`traefik.${YOUR_DOMAIN}.${YOUR_TLD}`) - traefik.http.services.traefik.loadbalancer.server.port=8080 - traefik.http.routers.traefik.entryPoints=websecure - traefik.http.routers.traefik.service=api@internal - traefik.http.routers.traefik.tls=true - traefik.http.routers.traefik.tls.certresolver=myresolver networks: default: name: proxy.bridge external: trueNotice that I'm using
proxy.bridgeas network. That way everything that you want to expose using Traefik reverse proxy needs to be in theproxy.bridgenetwork also for Traefik to detect their labels -
Click on
Deploy the stack, wait a bit forPortainerto download and run your container
How to open Traefik
- Open it using
http://your_device_ip:your_traefik_porti.e.http://192.168.1.1:8080 - OR since Traefik is a reverse proxy and we've setup the labels to use a custom domain and a working automatic certificate for it, open it using
https://traefik.your_domain.your_tldi.e.https://traefik.example.tld
How to use Traefik reverse proxy for other containers
-
Just add these labels to your services:
version: '3' services: service_name: ... labels: - traefik.enable=true - traefik.http.routers.traefik.rule=Host(`traefik.${YOUR_DOMAIN}.${YOUR_TLD}`) - traefik.http.services.${SERVICE_NAME}.loadbalancer.server.port=${SERVICE_INTERNAL_PORT} - traefik.http.routers.${ROUTER_NAME}.entryPoints=websecure - traefik.http.routers.${ROUTER_NAME}.service=api@internal - traefik.http.routers.${ROUTER_NAME}.tls=true - traefik.http.routers.${ROUTER_NAME}.tls.certresolver=myresolver -
In case of your service have multiple bridge networks attached, you need to specify Traefik network label, i.e.:
version: '3' services: service_name: ... labels: ... - traefik.docker.network=proxy.bridge -
Here is a working example with a simple Dozzle container:
version: '3' services: dozzle: container_name: dozzle volumes: - '/var/run/docker.sock:/var/run/docker.sock' restart: on-failure:5 image: 'amir20/dozzle:latest' labels: - traefik.enable=true - traefik.http.routers.dozzle.rule=Host(`dozzle.exampledomain.com`) - traefik.http.routers.dozzle.entrypoints=websecure - traefik.http.routers.dozzle.service=dozzle - traefik.http.services.dozzle.loadbalancer.server.port=8080 - traefik.http.routers.dozzle.tls=true - traefik.http.routers.dozzle.tls.certresolver=myresolver networks: default: name: proxy.bridge external: true
How to update Traefik
- In
Portainerclick onStacksthen click on yourTraefikstack - Click
Update the stack, toggle onRe-pull image and redeploythen clickUpdate
Important Links